VoWifi support
VoWifi feature is supported by default on Amari callboxes but usually this feature is locked at UE side when you use test sim card.
This wiki page aims to give you an idea about the VoWifi architecture, the configuration of different involved components and list the tricks that help to unlock the feature at UE side and test VoLTE feature using our callbox.
VoWifi Architecture
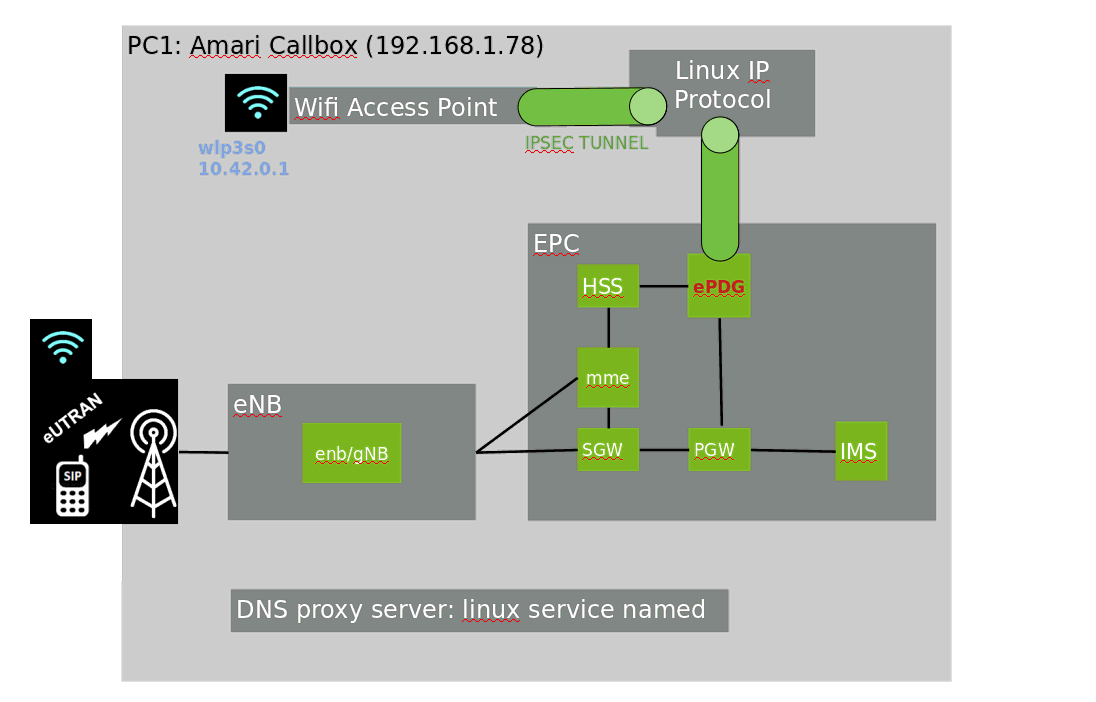
VoWifi option in phone menu
VoWifi option can be disabled by default in phone menu .
- Check that VoWifi option is enabled in phone setting menu > Mobile network > Mobile data > Wi-Fi Calling
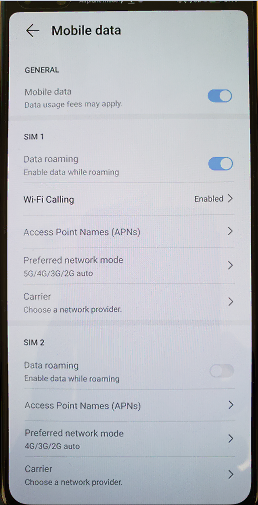
Note : Huawei P40 supports VoWifi feature only with commercial PLMN sim card.
Test SIM card
As explained above, some phones locks VoWifi feature in the case of test sim card.
Solution :
- Amarisoft Test sim card is a programmable sim card. Thus, using a simcard reader, you can easily change the imsi/mcc/mnc to a commercial imsi 20810:
Change IMSI/MCC/MNC
The following command sets the IMSI to 208100123456789 and home plmn to 20810:
./pySim-prog.py -p 0 --pin-adm=11111111 --mcc=208 --mnc=10 --imsi=208100123456789
For more details, you can also refer to following wiki page:https://extranet.amarisoft.com/wiki/doku.php?id=info:update
Note: It is important to update the mme ue db with the new sim card parameters.
Wifi Access Point Configuration on the Callbox
This session explains how to configure a Wifi Access Point on the callbox itself. If your callbox does not have an integrated Wifi mdoule (which is mostly the case for recent callboxes) you must add a Wifi USB dongle. Make sure that your dongle supports AP mode. Please note that you can also use an external WiFi router, in that case you do not need to enter the commands below, but you will have to add the DNS customization on the WiFi router or configure it to use the DNS server from the callbox. This kind of settings depends on the router that you use
Create a hotspot Wifi 'voWifi hotspot' on Fedora using Wifi interface wlp3s0
- use nmcli command to create the network connection:
nmcli con add type wifi ifname wlp3s0 con-name 'voWifi hotspot' autoconnect yes ssid 'voWifi hotspot'
- list the available connections:
sudo nmcli connection show
NAME UUID TYPE DEVICE
enp0s31f6 b5f59873-5bd2-c5a6-acb6-f03d5581aca5 ethernet enp0s31f6
tun0 2619c2b5-14be-43b8-a598-79663d2ab4e2 tun tun0
voWifi hotspot 3d4d6764-ae39-4f0e-84ff-15fcd2de1df8 wifi --
Wired connection 1 b141c172-48e8-3b74-8ef8-41aa57b6a207 ethernet --
- you can check if NetworkManager has added the config file to the network-scripts folder
[root@enb78-sophia ~]# ls -al /etc/sysconfig/network-scripts/
total 32
drwxr-xr-x. 2 root root 4096 5 nov. 09:56 .
drwxr-xr-x. 5 root root 4096 28 déc. 2020 ..
- rw-r--r--. 1 root root 365 6 oct. 09:56 ifcfg-enp0s31f6
- rw-r--r-- 1 root root 362 5 nov. 09:56 ifcfg-voWifi_hotspot
- rwxr-xr-x. 1 root root 2162 29 janv. 2020 ifdown-ipsec
- rwxr-xr-x. 1 root root 8981 29 janv. 2020 ifup-ipsec
- change the wifi connection infrastructure mode to AP:
sudo nmcli connection modify "voWifi hotspot" 802-11-wireless.mode ap 802-11-wireless.band bg ipv4.method shared
nmcli connection modify "voWifi hotspot" 802-11-wireless.mode ap 802-11-wireless-security.key-mgmt wpa-psk ipv4.method shared 802-11-wireless-security.psk 'PASSWORD'
- manually start the hotspot
sudo nmcli con up "voWifi hotspot"
Connection successfully activated (D-Bus active path: /org/freedesktop/NetworkManager/ActiveConnection/215)
- finally connect your device to wifi hotspot
DNS Proxy Configuration on a second machine
- to create a dns proxy server, you need to install bind-chroot package
dnf install bind-chroot
- then create the three files to /etc/named.conf /var/named/named.mydmn.org and /etc/named.rfc1912.zones as explained below:
- /etc/named.conf:
options {
listen-on port 53 { 10.42.0.1; 192.168.1.15; 127.0.0.1; }; // 10.42.0.1 is AP wifi ip addr, 192.168.1.15 is callbox ip addr
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
allow-query { any; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-validation yes;
managed-keys-directory "/var/named/dynamic";
geoip-directory "/usr/share/GeoIP";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
/* https://fedoraproject.org/wiki/Changes/CryptoPolicy */
include "/etc/crypto-policies/back-ends/bind.config";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
- /var/named/named.mydmn.org: set the mnc mcc of your "commercial" sim card. set also the wifi AP ip address
$TTL 86400
@ IN SOA ns1.epc.mnc010.mcc208.pub.3gppnetwork.org. root.epc.mnc010.mcc208.pub.3gppnetwork.org. (
20170423 ; serial
10800 ; refresh
3600 ; retry
604800 ; expire
86400 ; minimum
)
@ IN NS ns1.epc.mnc010.mcc208.pub.3gppnetwork.org.
@ IN A 10.42.0.1
ns1 IN A 10.42.0.1
epdg IN A 10.42.0.1
- /etc/named.rfc1912.zones: set the mnc mcc of your “commercial” sim card. set also the wifi AP ip address
zone "epc.mnc010.mcc208.pub.3gppnetwork.org" {
type master;
file "named.mydmn.org";
notify yes;
allow-update { none; };
};
- enable the service tuned (the service running the dns proxy):
systemctl enable named.service
systemctl start named.service
- test the dns proxy: from callbox machine run the following command, it should return the wifi AP ip address:
[root@enb78-sophia config]# nslookup epdg.epc.mnc010.mcc208.pub.3gppnetwork.org 10.42.0.1
Server: 10.42.0.1
Address: 10.42.0.1#53
Name: epdg.epc.mnc010.mcc208.pub.3gppnetwork.org
Address: 10.42.0.1
Start ePDG component on amarisoft callbox
ePDG component is running on amarisoft EPC ltemme binary. To configure ePDG, we have to:
- add the AP ip address to setup the tunnel between ePDG and AP wifi.
mme config file:
/* ePDG configuration */
epdg: {bind_addr: "10.42.0.1:500"},
- configure plmn on both mme and enb:
mme config file:
/* bind address for GTP-U. Normally = address of the PC, here bound
on local interface to be able to run ltemme on the same PC as
lteenb. By default, the S1AP SCTP connection is bound on the same
address. */
gtp_addr: "127.0.1.100",
plmn: "20810"
enb config file:
cell_list: [
{
/* Broadcasted PLMN identities */
plmn_list: [
"20810",
],
- then add the sim card parameter to mme ue db:
ue_db-ims.cfg config file:
{
sim_algo: "xor", /* USIM authentication algorithm: xor, milenage or tuak */
imsi: "208100123456789", /* Anritsu Test USIM */
amf: 0x9001, /* Authentication Management Field */
sqn: "000000000000", /* Sequence Number */
K: "00112233445566778899aabbccddeeff", /* Anritsu Test USIM */
impi: "208100123456789@ims.mnc010.mcc208.3gppnetwork.org",
impu: ["208100123456789", "tel:0600000000", "tel:600"],
domain: "ims.mnc010.mcc208.3gppnetwork.org",
multi_sim: true, /* Experimental */
/* For standard SIP client */
/*pwd: "amarisoft",
authent_type: "MD5",*/
},
VoWifi test and logs
to start VoWifi testing, you can proceed as following:
- on callbox machine, start a tcpdump on WiFi AP port:
tcpdump -i wlp3s0 -w /tmp/epdg-dns-proxy.pcap
- then, attach the phone to wifi AP
Then an icon "calls WiFi" is displayed on the phone:
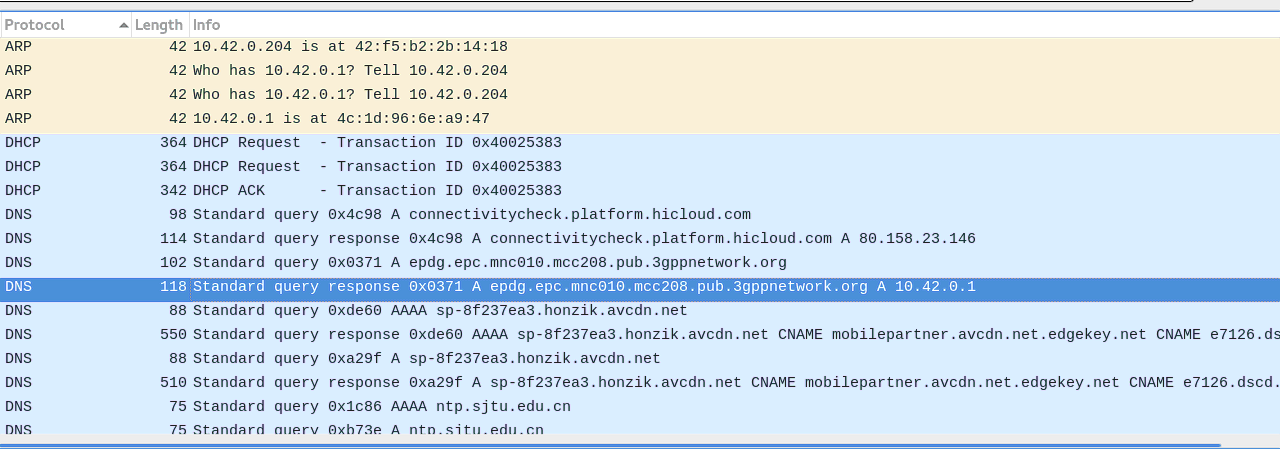
- bellow, the wireshark trace where we see the dns query to get epdg ip address
- finally, you can start an echo call by dialing 666



