NR SA ECC
The purpose of this tutorial is to show you how to configure ECC and test. ECC stands for Eliptic Curve Cryptography. It is the algorithm being used for SUPI <--> SUCI conversion. To improve security, it is not recommended to exchange UE IDs (e.g, IMSI) in plain text over the air. It is recommended to be encrypted before it is sent over the air. ECC is the algorithm that is used to convert the non-encrypted UE ID(SUPI) to encrypted UE ID(SUCI) and back and forth. Overall signaling flow for UE ID exchange is as illustrated below. In short, UE encrypt the SUPI into SUCI and send it to network via RegistrationRequest (or IdentityResponse when requested by Network) and it is get decrypted by UDM on corenetwork.
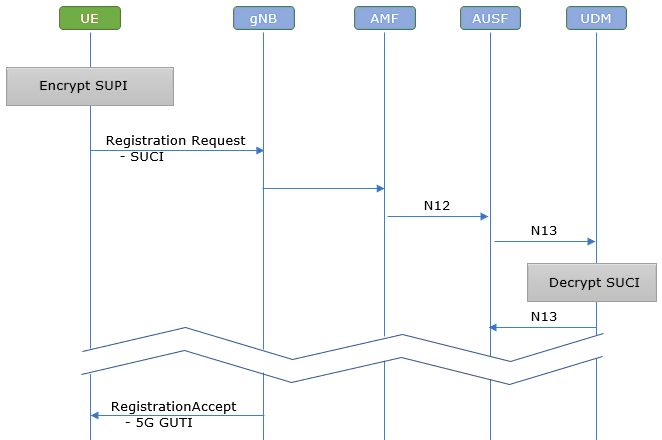
Table of Contents
Introduction
Elliptic Curve Cryptography (ECC) is a cornerstone of modern cryptographic security, renowned for providing strong encryption with relatively small key sizes, thus enabling efficient and secure communications over constrained channels. In the context of 5G mobile networks, ECC plays a vital role in safeguarding the privacy and security of user identities during network registration and authentication procedures. The Subscription Permanent Identifier (SUPI), which uniquely identifies a subscriber, must be protected from interception and unauthorized disclosure as it traverses the air interface. To this end, the SUPI is concealed using the Subscription Concealed Identifier (SUCI), a process underpinned by ECC-based encryption algorithms. This transformation ensures that sensitive user information is never transmitted in plaintext, mitigating risks such as identity theft and unauthorized tracking. The encryption and decryption mechanisms, based on standardized protocols like ECIES (Elliptic Curve Integrated Encryption Scheme), are implemented at both the User Equipment (UE) and the core network's Unified Data Management (UDM) entity. This architecture not only strengthens the security posture of next-generation mobile networks but also meets stringent regulatory and privacy requirements. By leveraging ECC, 5G systems achieve a robust balance between performance, scalability, and security, making the technology indispensable in the evolving telecommunications landscape.
-
Context of Elliptic Curve Cryptography (ECC) in 5G Networks
- ECC is integral to protecting subscriber identities by enabling secure SUPI-to-SUCI conversion.
- Used during critical signaling exchanges, such as network registration (e.g., RegistrationRequest, IdentityResponse), to ensure confidentiality over the air interface.
- Adopts industry-standard cryptographic protocols, ensuring interoperability and compliance with 3GPP specifications (notably TS 33.501).
-
Relevance and Importance of This Tutorial
- Addresses the industry's need to protect sensitive subscriber data in transit, aligning with privacy and security best practices.
- Guides practitioners through the configuration and testing of ECC-based SUPI/SUCI mechanisms in simulated or real 5G environments.
- Enhances understanding of the cryptographic processes that underpin modern mobile network security.
-
Learning Outcomes
- Gain practical knowledge of how to configure ECC for SUPI/SUCI encryption and decryption.
- Understand the end-to-end signaling flow for secure UE identity exchange in 5G networks.
- Acquire insights into the architectural role of ECC within the broader 5G security framework.
-
Prerequisites
- Familiarity with mobile network architecture (e.g., concepts such as UE, core network, UDM).
- Basic understanding of cryptographic principles and public key infrastructure.
- Awareness of 3GPP standards, especially those pertaining to security and identity management.
Summary of the Tutorial
This tutorial describes the procedure for testing the ECIES scheme profile A in a 5G standalone (SA) environment using Amarisoft Callbox and UEsim. The focus is on configuring the network and user equipment (UE) for ECIES authentication, performing the test, and validating the process through log analysis.
-
Test Setup:
- The test setup consists of a Callbox acting as the gNB and core network, and a UEsim representing the UE. The physical and logical connections are illustrated in the referenced diagram.
-
Key Configuration Parameters:
-
eNB/gNB configuration:
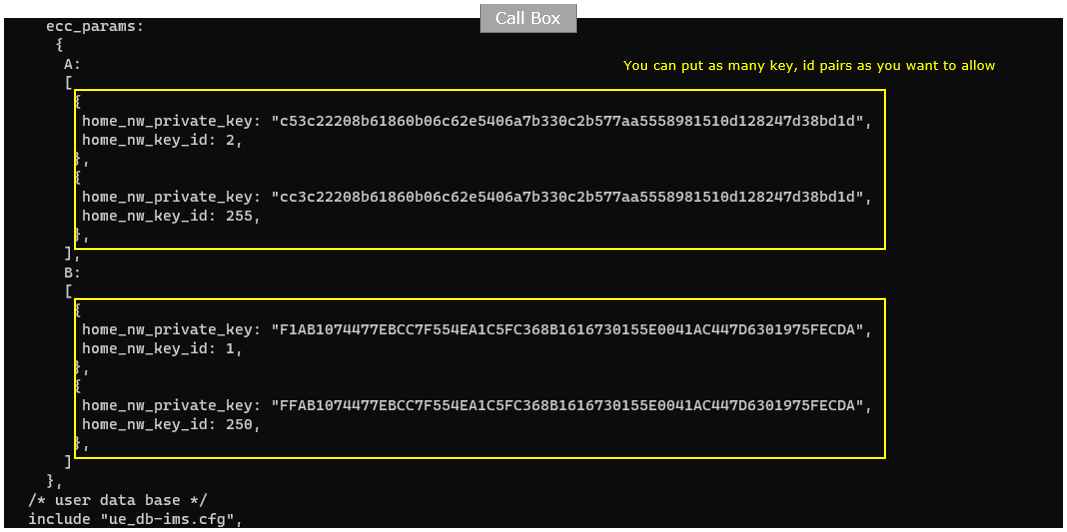
- Set ecc_params with multiple pairs of home_nw_private_key and home_nw_key_id for parameters “A” and “B”. Additional pairs can be added as needed for the test.
-
UE configuration:
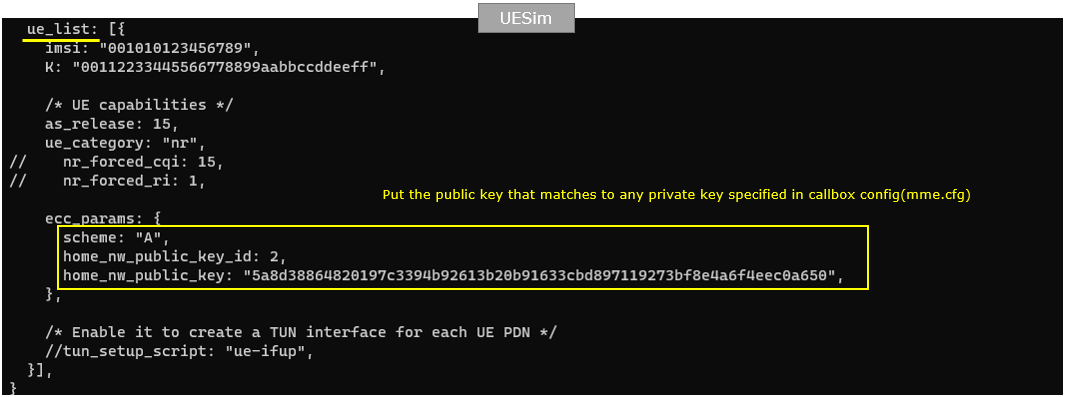
- Set ecc_params including scheme, home_nw_public_key, home_nw_public_key_id, and routing_indicator. Ensure the public key information matches one of the private keys configured in the network.
-
eNB/gNB configuration:
-
Test 1: ECIES Scheme Profile A
-
Configuration:
- Network Side (gNB/MME): Use a modified configuration file (mme-ims-ecc.cfg), derived from the default, with only relevant changes for ECC parameters.
- UE Side: Use a corresponding configuration file (ue-nr-sa-ecc.cfg), specifying the required public key and identifier.
- Ensure the key pairs between network and UE match for proper authentication.
-
Test Procedure:
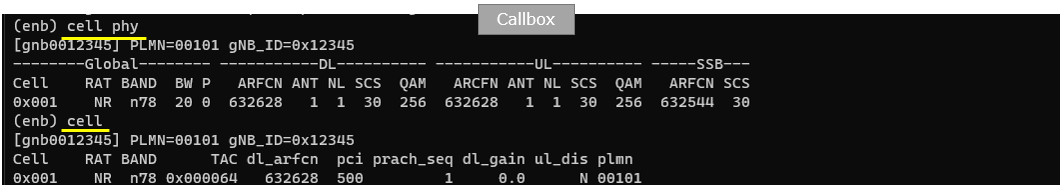
- Verify the cell is configured as intended on the Callbox/gNB.
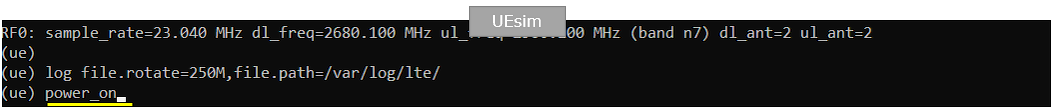
- Power on the UE using UEsim.
- Observe the UE performing attach procedures.
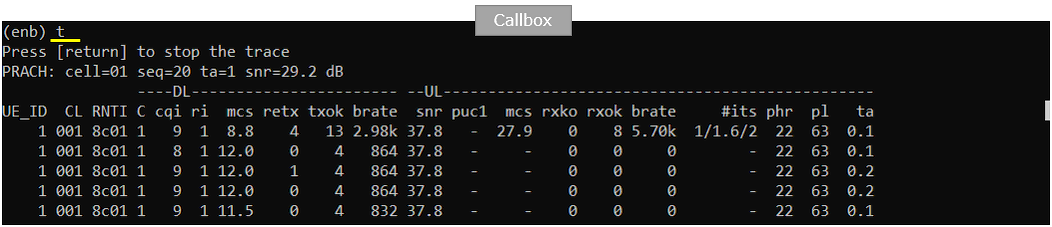
- Check and confirm that the UE successfully completes the attach and throughput is as expected.
-
Log Analysis:
- Confirm that the UE includes proper ECC parameters in the SUCI Information Element (IE) during the Registration Request.
- Verify that ECC information is transferred from the RAN to the core network via N12 interface.
- Ensure the AUSF (Authentication Server Function) verifies the ECC information with the UDM (User Data Management) over the N13 interface.
- Upon successful key verification, AUSF issues a status response allowing the AMF (Access Management Function) to trigger authentication.
-
Configuration:
This tutorial demonstrates the step-by-step configuration and validation for ECIES-based SUCI protection in a 5G SA scenario, focusing on key matching and proper signaling flow between UE and the core network.
Test Setup
Test setup for this tutorial is as shown below.

Key Configuration Parameters
Followings are important configuration parameters for this tutorial. You may click on the items for the descriptions from Amarisoft documents.
- enb configuration
- ecc_params
- A
- home_nw_private_key
- home_nw_key_id
- B
- home_nw_private_key
- home_nw_key_id
- ue configuration
- ecc_params
- scheme
- home_nw_public_key
- home_nw_public_key_id
- routing_indicator
Test 1 : ECIES scheme profile A
This test is to test ECIES scheme profile A
Configuration
I used the mme-ims-ecc.cfg on gNB which is copied and modified from mme-ims.cfg (NOTE : only mme.cfg is changed for this tutorial and all other configurations are default files)
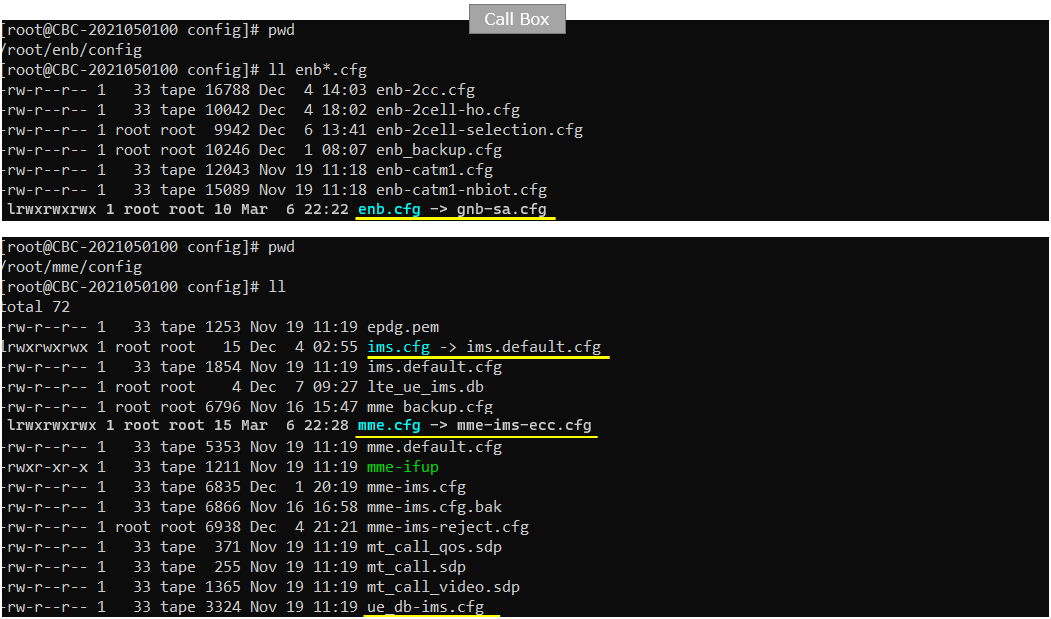
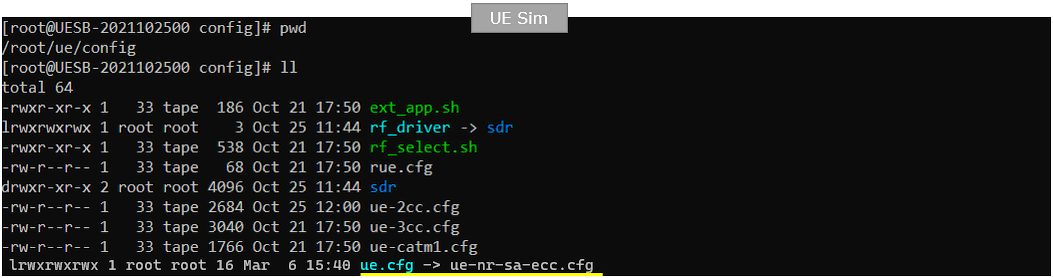
I used the ue-nr-sa-ecc.cfg on gNB which is copied and modified from ue-nr-sa.cfg
The mme configuration mme-ims-ecc.cfg is configured as follows. You just put pairs of home_nw_private_key and home_nw_key_id for the parameter A and B. You can put as many key, id pairs as you want to allow. (
In ue-nr-sa-ecc.cfg , the configuration is done as follows. You need to specify any public key information (home_nw_public_key_id and home_nw_public_key) that matches any of the private key specified in the callbox. (
Perform the Test
Check if the cell is configured as intended.
Power on UE on UE sim.
Confirm that the UE completes the attach and check the throughput.
Log Analysis
First when using ECC, UE is supposed to configure the proper ECC parameters in SUCI IE if Registration Request.
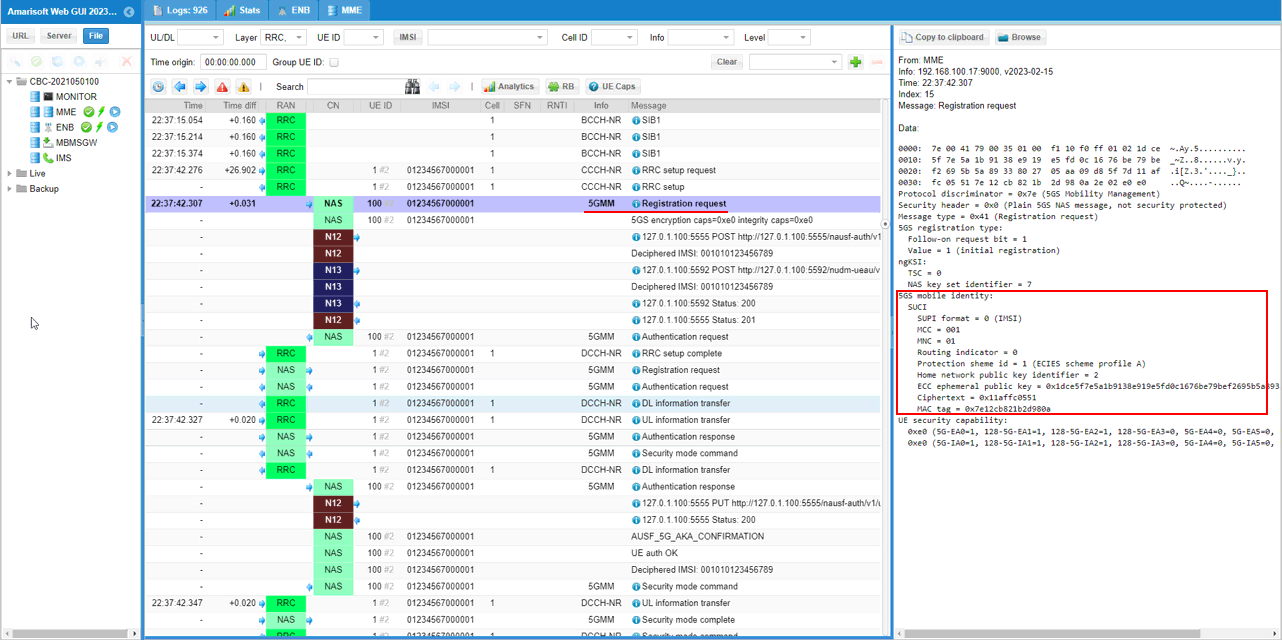
The ECC information (included in SUCI) is transferred to core network via N12 interface (the interface between AMF and AUSF).
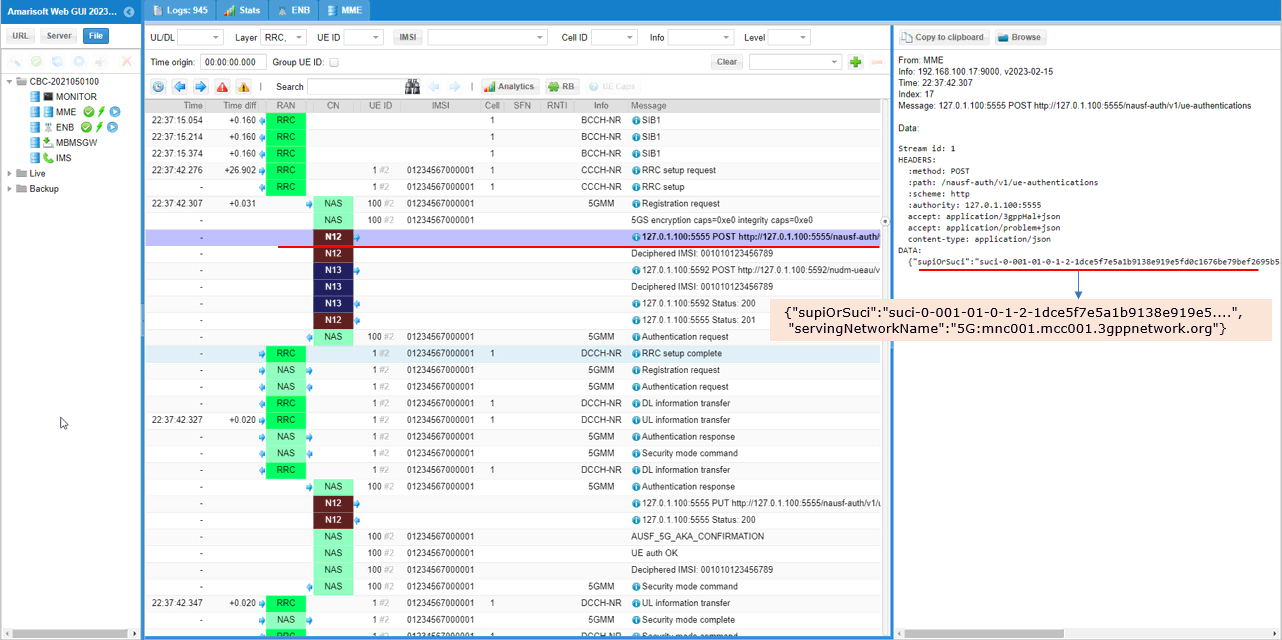
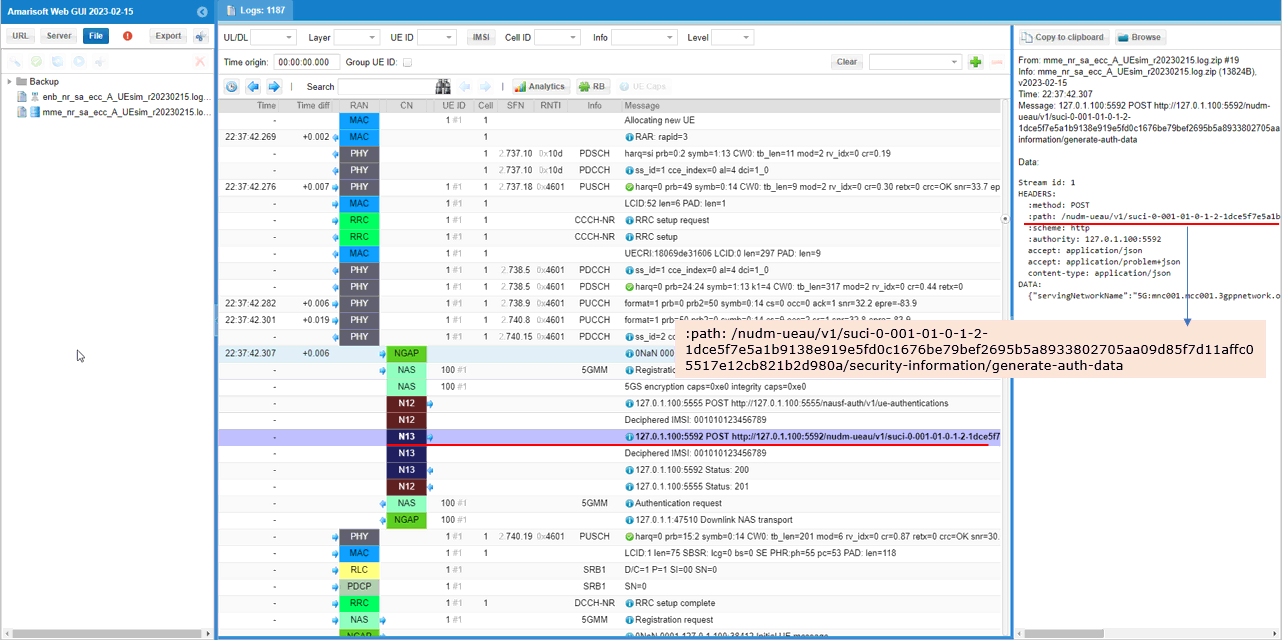
The AUSF verifies the information with UDM over N13 interface (the interface between AUSF and UDM).
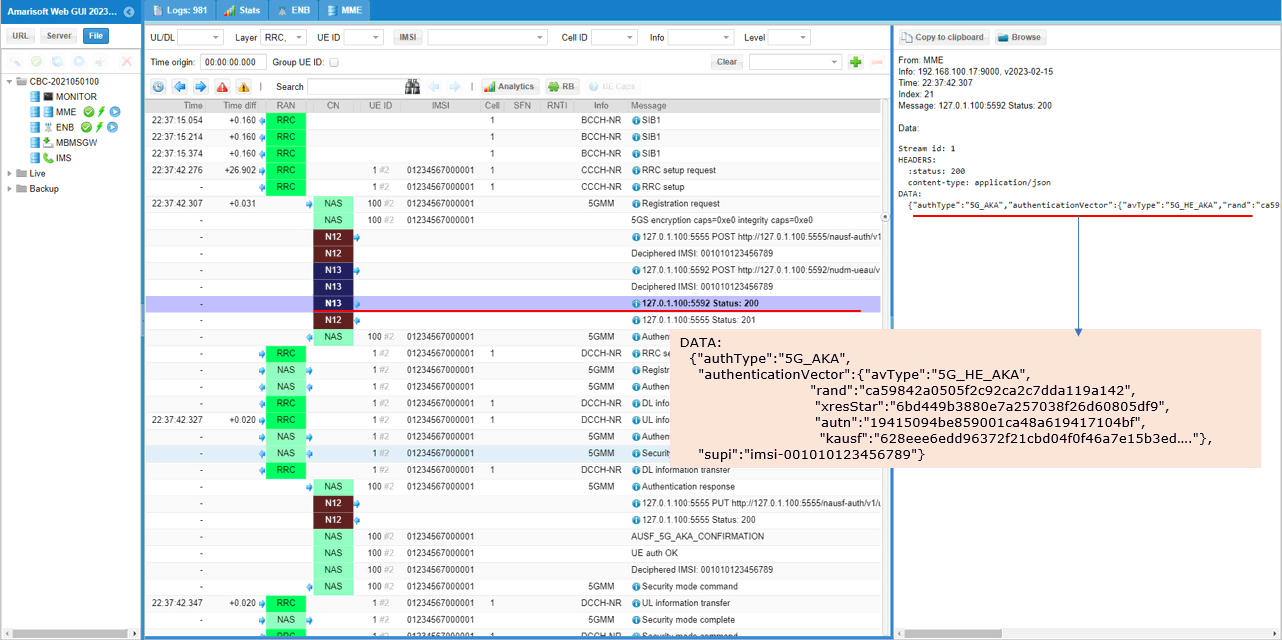
If the key is verified successfully, AUSF issues Status 200 with corresponding authentication key so that AMF trigger Authentication Request.
RRC / NAS Signaling
RegistraionRequest (SA)
: This is the RegistrationRequest sent by UE that should be decoded by Network (
Protocol discriminator = 0x7e (5GS Mobility Management)
Security header = 0x0 (Plain 5GS NAS message, not security protected)
Message type = 0x41 (Registration request)
5GS registration type:
Follow-on request bit = 1
Value = 1 (initial registration)
ngKSI:
TSC = 0
NAS key set identifier = 7
5GS mobile identity:
SUCI
SUPI format = 0 (IMSI)
MCC = 001
MNC = 01
Routing indicator = 0
Protection sheme id = 1 (ECIES scheme profile A)
Home network public key identifier = 2
ECC ephemeral public key = 0x1dce5f7e5a1b9138e919e5fd0c1676be79bef2695b5a8933802705aa09d85f7d
Ciphertext = 0x11affc0551
MAC tag = 0x7e12cb821b2d980a
UE security capability:
0xe0 (5G-EA0=1, 128-5G-EA1=1, 128-5G-EA2=1, 128-5G-EA3=0, 5G-EA4=0, 5G-EA5=0, 5G-EA6=0, 5G-EA7=0)
0xe0 (5G-IA0=1, 128-5G-IA1=1, 128-5G-IA2=1, 128-5G-IA3=0, 5G-IA4=0, 5G-IA5=0, 5G-IA6=0, 5G-IA7=0)